Hack.me The house of rising sandbox
OVERVIEW
HACK.ME TRAFFIC
Date Range
Date Range
Date Range
LINKS TO DOMAIN
Two phun phishing emails in two days. Both from the same domain, nac. net, which you might want to add to your block list. Yesterday is was a fake FBI email. This is another that falls into the ridiculous category, and maybe the get-rich-quick category as well. Why is the story a plot from a 90s movie? Throug.
Our blogs use real world examples that we believe offers a better understanding IT Security terms, process and hands on approach in a very straightforward way. Our aim is that all articles provide the reader a better understanding of the particular topics. Leave a Reply Cancel reply. Your email address will not be published. Your PORN DOES NOT IMPRESS US! Why is my Doctor trying to KILL ME? IOS 11.
Questions to Ask BEFORE a Public Speaking Engagement.
By using this virtual machine, you agree that in no event will I be liable for any loss or damage including without limitation, indirect or consequential loss or damage, or any loss or damage whatsoever arising from loss of data or profits arising out of or in connection with the use of this software. Brainpan 3 has been tested and found to work with VMware Player, VMware Fusion, and Virtual Box.
Is an open source tool to audit wireless networks. It allows the user to deploy advanced attacks by directly using the web interface or by sending messages to it. REMnux Usage Tips for Malware Analysis on Linux. Key tools and commands for analyzing malicious software on the REMnux Linux distribution. Critical Log Review Checklist for Security Incidents.
0 x86 phfont - Local root Exploit. 0 x86 io-graphics - Local root Exploit. Buffer Overflow - Definition, detection and remediation.
WHAT DOES HACK.ME LOOK LIKE?
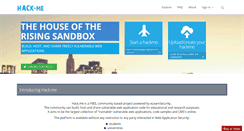

HACK.ME SERVER
BROWSER IMAGE
SERVER OS
We observed that this domain is using the Microsoft-IIS/7.5 server.HTML TITLE
Hack.me The house of rising sandboxDESCRIPTION
Hack.me is a free community based project powered by eLearnSecurity. The community can build, host and share vulnerable web application code for educational and research purposes.The platform is available without any restriction to any party interested in Web Application Security students, universities, researchers, penetration testers and web developers.PARSED CONTENT
The domain hack.me states the following, "The house of the rising sandbox." We observed that the webpage also said " Build, host, and share freely vulnerable web applications." It also stated " Run a vulnerable web app on-the-fly. Share your skills with the community. Hackme is a FREE, community based project powered by eLearnSecurity. The community can build, host and share vulnerable web application code for educational and research purposes. It aims to be the largest collection of runnable vulnerable web applications, code samples and CMSs online. Theres no need to give further explanations!." The header had hack.me as the highest ranking keyword. This keyword was followed by hackme, hack me, and hacker which isn't as urgent as hack.me. The other words the site used was hackers. hack is also included but might not be viewed by web engines.SEEK OTHER WEB SITES
دانلود بهترین نرم افزارهای هک و سکیوریتی. دانلود بهترین نرم افزارهای هک و سکیوریتی. دانلود بهترین نرم افزارهای هک و سکیوریتی. MortalKombat Forum Spammer - نرم افزار تبلیغ در انجمن های گفتگو.
Create your own army! Choose your first trooper! Do you already have an army? 16 crew, 2 traitors. Seek, destroy, survive. As the TEACHER! Welcome to the scores war. Pocket Amazon vouchers! Could you run a hotel where every guest is monstrous? .
The Temple of the Moby Hack is the shared computer and network resources of a few friends and acquaintances. Some of us might be computer hackers. In the old meaning of computer enthusiasts but most of our users simply prefer using the non-commercial hack.
Please contact your service provider for more details.